- Published on
AWS: IAM and Best Practices
- Authors
- Name
- Full Stack Engineer
- @fse_pro
Amazon Web Services (AWS) Identity and Access Management (IAM) is a crucial service that enables you to manage access to AWS resources securely. Implementing IAM best practices is essential for maintaining a robust and secure cloud environment. In this guide, we'll delve into IAM and discuss key best practices.
Understanding AWS IAM
IAM allows you to control who can access your AWS resources and what actions they can perform. Key components of IAM include users, groups, roles, and policies. Users represent individuals or services, groups are collections of users with shared permissions, roles define a set of permissions for trusted entities, and policies are JSON documents that specify permissions.
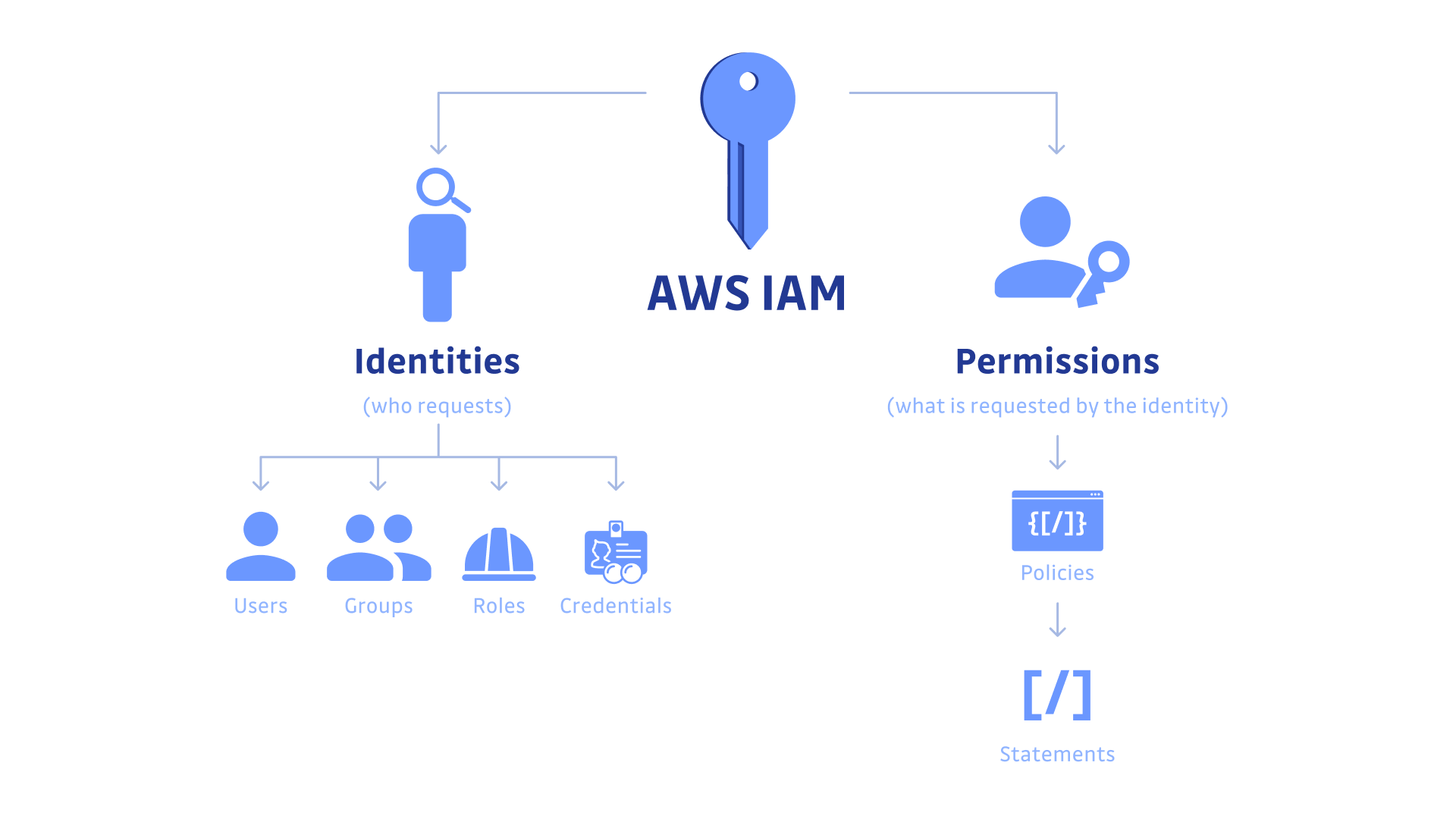
IAM Best Practices
1. Principle of Least Privilege (PoLP)
Follow the PoLP by granting users and processes the minimum access required to perform their tasks. Regularly review and adjust permissions to align with job responsibilities.
2. Use IAM Roles for AWS Resources
Instead of sharing access keys, use IAM roles for applications running on AWS resources. Roles provide temporary security credentials and help implement secure access between AWS services.
3. Multi-Factor Authentication (MFA)
Enable MFA for IAM users to add an extra layer of security. This ensures that even if credentials are compromised, an additional factor is required for access.
4. Regularly Rotate Access Keys
Rotate access keys periodically to enhance security. AWS provides tools and APIs to automate key rotation for IAM users.
5. Monitor and Audit IAM Usage
Utilize AWS CloudTrail to monitor and log IAM actions. Regularly review these logs to detect and respond to any unauthorized or suspicious activities.
6. Organize Users with IAM Groups
Group users with similar job responsibilities into IAM groups. This simplifies permission management, allowing you to apply policies to multiple users at once.
7. Use IAM Policy Conditions
Implement conditions in IAM policies to control when policies are in effect. Conditions add an extra layer of control over access and are useful for specific scenarios.
8. Secure Access to AWS Management Console
Restrict access to the AWS Management Console based on IP addresses and use IAM roles for cross-account access.
Conclusion
AWS IAM is a powerful tool for managing access to AWS services securely. By implementing these best practices, you can enhance the security posture of your AWS environment and mitigate potential risks.